Aula Aberta: Mestrado / Curso de Especialização em Epidemiologia
“Informática Médica e suas aplicações no Sistema de Saúde, na Saúde Pública e na Epidemiologia“
Formulário de inscrição aqui
Data: 5ªf, 20 julho 17h30 – 20h50 (Hora de Lisboa)
Tópicos:
Nesta aula aberta iremos abordar vários tópicos relevantes para ser compreender o vasto âmbito da informática médica, como:
- O que é a informática médica e que dimensões integra?
- Os dados biomédicos, seus tipos, características e contextos de produção.
- Sistemas clínicos.
- Terminologias, sistemas de classificação e ontologias biomédicas.
- Aplicações da informática médica, como a telemedicina, a telemedicina ou a simulação médica.
- Os sistemas de informação no Serviço Nacional de Saúde Português.
- Do uso da informática médica na Saúde Pública e a sua relação com as funções da Saúde Pública.
- Os sistemas de informação em Saúde Pública: vigilância, geomonitorização, a integração de sistemas, o ‘big data’.
- A genómica e a medicina de precisão.
- Os desafios da Informática na Saúde Pública.
Docente: Professor Doutor Mário Silva
Professor Catedrático do Departamento de Informática do IST e investigador do INESC-ID. Realizou o seu doutoramento na Universidade de Berkeley em 1994, após um bacharelado e um mestrado pelo IST, em 1983 e 1987, respetivamente. As suas principais áreas de interesse são a Engenharia de Sistemas de Informação baseados na Web, o processamento de linguagem natural (como a pesquisa e prospeção de texto, integração de informação biológica e geográfica), bem como aplicações em informática biomédica.
Formulário de Inscrição: Poderá inscrever-se através deste link
Sessão Online de Apresentação e Esclarecimento
no âmbito do XIII Mestrado 2023-25 / IV Curso de Especialização em Epidemiologia 2023-24 (à distância)
Data: 3ªf, 18 julho das 18h00 às 19h30 (hora de Lisboa – à distância em tempo real)
Como se inscrever? Poderá inscrever-se através do formulário de inscrições aqui
| Esta sessão de apresentação e esclarecimento abordará a: XIII Edição do Mestrado em Epidemiologia 2023-25 e a IV Edição do Curso de Especialização em Epidemiologia 2023-24 (à distância) – (formação à distância com o mesmo Plano de Estudos que o 1º ano do Mestrado em Epidemiologia) |
| Nesta sessão terá resposta a todas as questões sobre o Mestrado em Epidemiologia / Curso de Especialização em Epidemiologia (à distância) tais como: |
| 1. O que se aprende, que competências, que modelo de formação? 2. Como são organizadas as sessões? 3. Posso repartir as unidades curriculares e realizar o ano curricular / Curso de Especialização em 2 anos? 4. Qual o valor e os critérios de atribuição das Bolsas de Apoio? 5. Que teses têm sido desenvolvidas? Cursos e conteúdos obrigatório e opcionais. 6. Quais as oportunidades atuais de emprego e para se desenvolver investigação clínica e epidemiológica? |
Poderá também consultar o breve vídeo de apresentação ao Mestrado em Epidemiologia aqui ou na imagem abaixo:
Poderá também ter acesso ao programa, cursos e aulas abertas, dissertações que têm vindo a ser realizadas e às FAQ (Frequently Asked Questions), através dos links abaixo:
Apresentação e Programa | Cursos e Aulas Abertas | Dissertações | FAQ
Para mais informações, contacte nos através do email: mepidemiologia@medicina.ulisboa.pt
Aula Aberta: Mestrado/Curso de Especialização em Epidemiologia
“Uso do excel na investigação: tabelas de dados, tabelas dinâmicas e outras dicas úteis“
Data: 5ªf, 13 julho 17h30 – 20h50 (Hora de Lisboa)
Tópicos:
- Introdução às principais funções do Excel
- Ligação entre tabelas de dados
- Produção de tabelas dinâmicas
- Criação de dashboards dinâmicos
Docente: Professora Matilde Valente Rosa
Licenciada em Matemática Aplicada e Computação pelo Instituto Superior Técnico, Universidade Técnica de Lisboa (2011). Mestre em Estatística pela University of Bristol (2012) e Pós-Graduada em Dinâmica de Sistemas pela Universitat Politècnica de Catalunya (2011, 2016). Consultora da Direção-Geral da Saúde, na Direção de Serviços de Informação e Análise (2012 – 2014, 2017). Professora Convidada da Faculdade de Medicina da Universidade de Lisboa. Fundadora da Social Data Lab (2014), uma empresa que se dedica à produção e análise estatística da informação, utilizando o BI e o Machine Learning para apoio à decisão.
Formulário de Inscrição: Poderá inscrever-se através deste link
Sessão Científica: “Avaliação das Competências Não Técnicas das Equipas de Saúde de Emergência do Extra-Hospitalar da Delegação Regional do Algarve” Discussão de Protocolo
Data: 3ªf, 11 julho 18h00 – 19h30 (Hora de Lisboa)
Resumo:
As Competências não Técnicas (CNT) podem ser definidas como as competências cognitivas, sociais e interpessoais que complementam as competências técnicas e contribuem para o desempenho seguro e eficiente da tarefa.
O projeto pretende servir de base ao estudo das CNT no desempenho das Equipa de Saúde de Emergência do Extra-Hospitalar, em ambiente simulado de formação, com o intuito de monitorizar e avaliar novos modelos de formação ou de organização de recursos nas equipas de emergência (humanos e materiais).
Preletores: Dr.ª Georgina Pimentel, Dr.ª Sandra Nunes e Dr. Vasco Monteiro
Alunos do Curso Pós-Graduado de Abordagem Prática à Investigação Epidemiológica: Espaço-Projeto
Formulário de Inscrição: Poderá inscrever-se através deste link
Aula Aberta: Mestrado/Curso de Especialização em Epidemiologia
“Avaliação de Impacto em Saúde”
Data: 2ªf, 10 julho 14h30 – 18h00 (Hora de Lisboa)
Tópicos:
- Introdução à Avaliação de Impacte na Saúde
- Definição, Objectivo principal
- Exemplo: Pandemia Covid19
- Determinantes Sociais de Saúde, Equidade e Saúde em todas as políticas
- Avaliação de Impacte na Saúde (AIS – HIA Health Impact Assessment)
- Origens
- Etapas, Tipos e Timings
- Vantagens e Desvantagens Exemplos Caso Prático – trabalho em grupos
Docente: Professora Doutora Leonor Bacelar Nicolau
Leonor Bacelar Nicolau tem dois Doutoramentos, em Organização e Gestão da Saúde pela Faculdade de Medicina de Lisboa (FMUL – Portugal) e em Economia da Saúde pelo Conservatoire National des Arts et Métiers(CNAM – França), um mestrado em Estatística e Gestão da Informação pela NOVA IMS Information Management School e uma licenciatura em Economia pela NOVA School of Business and Economics (Portugal).
É Professora e investigadora convidada na FMUL (Instituto de Medicina Preventiva e Saúde Pública, ISAMB – Instituto de Saúde Ambiental, e EpiTaskForce) desde 2004, colaborando também com a NOVA IMS a nível de pós-graduação (2002-2006 e desde 2017). É sócia fundadora da DataScience Cons. desde 2001, onde é responsável pelas áreas de análise de negócios, avaliação digital e investigação de inovação metodológica.
Formulário de Inscrição: Poderá inscrever-se através deste link
Sessão Científica
“Avaliação e identificação dos preditores de qualidade de vida relacionado com a saúde nos doentes após enfarte agudo do miocárdio” Discussão de protocolo
Data: 3ªf, 20 junho 18h00 – 19h30 (Hora de Lisboa)
Resumo da Sessão:
Nesta sessão de discussão de protocolo de investigação será apresentado o estudo, metodologia preconizada e impacto esperado.
Através da medição da qualidade de vida relacionada com a saúde através do questionário de MacNew, este estudo pretende compreender o impacto da revascularização coronária na qualidade de vida, bem como identificar fatores que influenciam a auto-percepção da qualidade de vida nos indivíduos após enfarte agudo do miocárdio.
Preletores: António Cristóvão, Camila Sevegnani, Fernanda Rodrigues
Alunos do IX Curso Pós-Graduado Espaço- Projeto: Abordagem Prática à Investigação Clínica
Formulário de Inscrição: Poderá inscrever-se através deste link
Sessão Científica
“Cardiovascular Risk Factors and Morbidity in Systemic Autoimmune Diseases”
Data: 4ªf, 7 junho 18h00 – 19h30 (Hora de Lisboa/Lisbon Time)
Resumo da sessão: Cardiovascular diseases (CVDs) include numerous conditions associated with a high and growing worldwide global burden, representing the most common cause of death. Immune-mediated and inflammatory diseases (IMIDs) are associated with higher cardiovascular morbidity and mortality rates. Although IMIDs can be associated with a higher prevalence of well-known cardiovascular risk factors, such as metabolic syndrome, smoking, type 2 diabetes, and obesity, these factors do not fully account for the greater prevalence and incidence of CVDs. In this session, we will present our project which aims to evaluate the prevalence of CVD in systemic autoimmune diseases, the contribution of different demographic and disease-related variables and traditional cardiovascular risk factors in the prevalence of CVD and determine the perception of patients regarding the CV risk inherent to their diagnosis.
Preletores: Cristiana Sieiro Santos, Maria Oliveira, Paulo Ney Solari, Pedro Mateus
Alunos do Curso de Especialização em Epidemiologia da FMUL
Formulário de Inscrição: Poderá inscrever-se através deste link
Sessão Científica
“Doenças Neurodegenerativas e Força de Preensão Manual na População Europeia”
Data: 2ªf, 12 junho 18h00 – 19h30 (Hora de Lisboa) – À distância, em tempo real
Resumo da sessão:
Nesta sessão serão apresentados os resultados preliminares de um estudo que pretende analisar a relação entre a força e o diagnóstico de doenças neurodegenerativas. Esta investigação tem como foco de estudo a doença de Alzheimer e a doença de Parkinson e a sua relação com a força de preensão manual. Os dados analisados foram obtidos durante a wave 7 do SHARE, o Inquérito Europeu de Saúde, Envelhecimento e Reforma.
Preletora: Luísa Barateiro
Mestranda em Epidemiologia pela FMUL e Mestranda em Saúde Pública pela FMUP. Pós-graduada em Ciências Forenses, Investigação Criminal e Comportamento Desviante pelo Instituto CRIAP. Licenciada em Biologia pela Universidade de Aveiro. Possui vasta formação no domínio da saúde, segurança internacional e gestão de crises, das quais se destaca o Curso de Gestão de Crises do Instituto da Defesa Nacional. Atualmente é formadora na ISO-SEC na área da saúde em catástrofes e crises humanitárias e violência com base no género.
Formulário de Inscrição: Poderá inscrever-se na sessão através do link.
Inscrições Abertas
XII Curso Pós-Graduado de Ensaios Clínicos (à distância)
Onde? À distância, em tempo real
Quando? 19, 21, 23, 26, 28 e 30 de junho; 3, 5, 7, 10, 12, 14, 17, 19, 21, 24 e 26 de julho, das 18h00 às 20h50 (horas de Lisboa)
Como se inscrever? Registe o seu interesse no formulário de pré-inscrição (link). Ser-lhe-à, posteriormente, enviado um formulário de inscrição. Será necessário juntar: CV resumido, carta de motivação, certificado de licenciatura/mestrado (digitalizado) e comprovativo de pagamento.
Qual o valor e prazo da inscrição? Até 9 de jun, a inscrição é de 325€. Após 9 de jun, o valor será de 400€
Quais são as condições para a atribuição de Bolsa UEPID? Será atribuída 1 Bolsa UEPID, no valor de 75% da inscrição. Poderá consultar o regulamento da Bolsa aqui
Para mais informações poderá visitar a página do curso aqui ou contactar-nos pelo email: mepidemiologia@medicina.ulisboa.pt
Linkedin UEPID
No Linkedin da Unidade de Epidemiologia poderá encontrar informações sobre: Formação Pós-Graduada, Oportunidades de Financiamento: Bolsas e Prémios de Investigação, Sessões Científicas, Aulas Abertas, Webinares…
Para saber mais, visite o Linkedin UEPID aqui
Sessão de Esclarecimento e de Apresentação:
XIII Mestrado em Epidemiologia 2023-25 / IV Curso de Especialização em Epidemiologia 2023-24 (à distância)
Esta sessão de apresentação e esclarecimento abordará a:
– 13ª Edição do Mestrado em Epidemiologia 2023-25
– 4ª Edição do Curso de Especialização em Epidemiologia 2023-24 (à distância) (formação com o mesmo Plano de Estudos que o 1º ano do Mestrado em Epidemiologia)
(Formação com o mesmo Plano de Estudos que o 1º ano do Mestrado em Epidemiologia)
Quando? 5ªf, 25 maio, das 17h30 às 18h30 (Hora de Lisboa)
Onde? À distância, em tempo real
Inscrição aberta: Inscrição livre, mas obrigatória – formulário – Irá receber por email um link de acesso 1h antes da sessão
Nesta sessão de esclarecimento terá resposta a todas as questões sobre o Mestrado em Epidemiologia / Curso de Especialização em Epidemiologia (à distância):
- O que se aprende, que competências, que modelo de formação?
- Como são organizadas as sessões?
- Posso repartir as unidades curriculares e realizar o ano curricular / Curso de Especialização em 2 anos?
- Qual o valor e os critérios de atribuição das Bolsas de Apoio?
- Que teses têm sido desenvolvidas? Cursos e conteúdos obrigatório e opcionais.
- Quais as oportunidades atuais de emprego e para se desenvolver investigação clínica e epidemiológica?
Para saber mais sobre o Mestrado/Curso de Especialização em Epidemiologia poderá ver o vídeo aqui
APRESENTAÇÃO E PROGRAMA | CURSOS E AULAS ABERTAS | DISSERTAÇÕES | FAQ
Para mais informações, contacte-nos pelo email: mepidemiologia@medicina.ulisboa.pt
Webinar aberto: Realidades na Gestão de Projetos de Investigação na Saúde (à distância)
Quando? 4ªf, 24 de maio, das 18h00 às 20h00 (hora de Lisboa)
Onde? À distância, em tempo real
Como se inscrever? Poderá inscrever-se através do formulário aqui. Posteriormente receberá o link de acesso à sessão zoom.
O webinar aberto com o tema: “Realidades na Gestão de Projetos de Investigação na Saúde” terá a presença das seguintes preletoras:
– Inês Cabrita: CRO Académica (CETERA/AIDFM)
– Lurdes Conceição: Gabinete de Investigação (ITQB NOVA)
– Luísa Alexandra Sal: Gabinete de uma Faculdade (Universidade de Aveiro)
– Isabel Carvalho Oliveira: AICIB (Agência e dInvestigação Clínica e Inovação Biomédica)
– Maria João Gomes Santos: Consultora (Evidenze Portugal)
Para mais informações, contacte-nos pelo email: mepidemiologia@medicina.ulisboa.pt
Newsletter UEPID
Poderá ter acesso a informações sobre a formação pós-graduada, sessões científicas organizadas pelos nossos alunos do Mestrado, aulas abertas, oportunidades de financiamento, de emprego e a muito mais através da Newsletter UEPID!
Para subscrever à Newsletter aceda ao link aqui
Para mais informações poderá contactar-nos pelo email: mepidemiologia@medicina.ulisboa.pt
Aula Aberta: Mestrado / Curso de Especialização em Epidemiologia: “A comunicação e discussão social de resultados científicos”
Quando? 2ªf, 8 maio, das 16h às 17h
Onde? À distância, em tempo real.
Inscrição aberta: Inscrição livre, mas obrigatória através do formulário aqui
Resumo: A disseminação de resultados científicos para o grande público através dos media pressupõe comunicação entre cientistas e jornalistas, um processo que põe frente a frente dois mundos à parte, com interesses e objectivos bem distintos. É possível conciliá-los, servindo o público com informação rigorosa e interessante? O que podem os cientistas aprender com os jornalistas e vice-versa?
Sobre o docente: António Granado é professor auxiliar na Universidade Nova de Lisboa, onde está desde 2006. É jornalista de ciência há mais de 27 anos. Foi professor de Jornalismo na Universidade de Coimbra entre 1996 e 2006, e fez a maior parte da sua carreira no jornal Público, onde foi jornalista, editor, chefe de redacção e sub-director. Entre Setembro de 2010 e Março de 2014 foi responsável da área multimédia da Direcção de Informação da RTP.
É coordenador do mestrado em Jornalismo e do mestrado em Comunicação em Ciência (parceria ITQB NOVA/NOVA FCSH) e investigador com interesses na área do Jornalismo Digital e da Comunicação de Ciência.
Contamos com a sua presença na aula aberta!
Inscrições abertas
XIII Workshop de Análise Multifatorial em Epidemiologia
Onde? À distância, em tempo real
Quando? 18, 22, 25, 29 de maio e 1 de junho de 2023 – 2ªfs das 14h30 às 18h e 5ªfs das 17h30 às 20h50 (horário de Lisboa).
Como se inscrever? Registe o seu interesse no formulário de pré-inscrição (link). Ser-lhe-à, posteriormente, enviado um formulário de inscrição. Será necessário juntar: CV resumido, carta de motivação, certificado de licenciatura/mestrado (digitalizado) e comprovativo de pagamento.
Qual o valor e prazo da inscrição? Até 9 maio, o valor da inscrição é de 250€. Após 9 de maio, o valor da inscrição será de 350€.
Quais são as condições para a atribuição de Bolsa UEPID? Será atribuída 1 Bolsa UEPID, no valor de 75% da inscrição. Poderá consultar o regulamento da Bolsa aqui
Para mais informações poderá visitar a página do curso aqui ou contactar-nos pelo email: mepidemiologia@medicina.ulisboa.pt
Inscrições abertas
XII Curso Pós-Graduado de Análise Multifatorial em Epidemiologia (à distância)
Onde? À distância, em tempo real
Quando? 9, 10, 16, 17, 23, 26 e 30 de Maio, 2, 16 e 20 de Junho de 2023 das 18h às 20h50 (horário de Lisboa).
Como se inscrever? Registe o seu interesse no formulário de pré-inscrição (link). Ser-lhe-à, posteriormente, enviado um formulário de inscrição. Será necessário juntar: CV resumido, carta de motivação, certificado de licenciatura/mestrado (digitalizado) e comprovativo de pagamento.
Qual o valor e prazo da inscrição? Até 4 maio, o valor da inscrição é de 280€. Após 4 de maio, o valor da inscrição será de 350€.
Quais são as condições para a atribuição de Bolsa UEPID? Será atribuída 1 Bolsa UEPID, no valor de 75% da inscrição. Poderá consultar o regulamento da Bolsa aqui
Para mais informações poderá visitar a página do curso aqui ou contactar-nos pelo email: mepidemiologia@medicina.ulisboa.pt
Aula Aberta do Mestrado / Curso de Especialização em Epidemiologia: “Aspetos Legais e processuais da Proteção de Dados do ponto de vista do investigador”
Preletor: Tiago Abade
Advogado Coordenador da Área de Direito Público, Regulatório e Privacy da CCR
Legal – PwC Legal EDP / DPO
Quando? 5ªf, 27 de abril, das 19h50 às 20h50
Onde? à distância, em tempo real
Inscrição gratuita: Inscrição livre, mas obrigatória através do link
Pré-inscrições abertas
XII Curso Pós-Graduado de Análise Multifatorial em Epidemiologia (à distância)
Onde? À distância, em tempo real
Quando? 9, 10, 16, 17, 23, 26 e 30 de Maio, 2, 16 e 20 de Junho de 2023 das 18h às 20h50 (horário de Lisboa).
Como se inscrever? Registe o seu interesse no formulário de pré-inscrição (link). Ser-lhe-à, posteriormente, enviado um formulário de inscrição. Será necessário juntar: CV resumido, carta de motivação, certificado de licenciatura/mestrado (digitalizado) e comprovativo de pagamento.
Qual o valor e prazo da inscrição? Até 4 maio, o valor da inscrição é de 280€. Após 4 de maio, o valor da inscrição será de 350€.
Quais são as condições para a atribuição de Bolsa UEPID? Será atribuída 1 Bolsa UEPID, no valor de 75% da inscrição. Poderá consultar o regulamento da Bolsa aqui
Para mais informações poderá visitar a página do curso aqui ou contactar-nos pelo email: mepidemiologia@medicina.ulisboa.pt
Inscrições Abertas
I Curso / II Workshop de Gestão de Projetos Científicos em Saúde
A Unidade de Epidemiologia do Instituto de Medicina Preventiva e Saúde Pública (IMP&SP) encontra-se a realizar o I Curso / II Workshop de Gestão de Projetos Científicos em Saúde (online).
Quando?
O curso realizar-se-à de 2 de maio a 6 de junho.
Curso (Componente Teórica + Laboratório de Competências): 3ªfs (18h00 -20h50) – 2, 9, 16, 23, 30 de maio e 6 de junho de 2023 e 6ªfs (18h00 – 20h50) – 5, 12, 19, 26 de maio e 2 de junho de 2023
Workshop (Componente Teórica): 3ªfs (18h00 -20h50) – 2, 9, 16, 23, 30 de maio e 6 de junho de 2023
Seminário – (18h00 -20h00) – 24 de maio (4ªf)
Como se inscrever? Poderá efetivar a sua inscrição através do formulário de inscrições aqui. Terá de anexar os seguintes documentos: CV, Certificado de Habilitações, Comprovativo de Pagamento e Carta de Motivação.
Qual o valor e prazo da inscrição?
Curso (Componente Teórica + Laboratório de Competências) – Até 22 de Abril de 2023, o valor será de 220€. Após esta data, a inscrição será de 320€.
Workshop (Componente Teórica) – Até 22 de Abril de 2023, o valor será de 170€. Após esta data, a inscrição é de 280€
Quais são as condições para a atribuição de Bolsa UEPID? Será atribuída até 1 Bolsa de Formação para o Curso e para o Workshop, no valor de 75% da inscrição. Para mais informações consulte o link
Poderá consultar o programa completo com os docentes aqui.
Para mais informações poderá visitar a página do curso aqui ou contactar-nos pelo email: mepidemiologia@medicina.ulisboa.pt
Inscrições Abertas
X Workshop de Introdução à Plataforma Estatística R
Onde? À distância (em tempo real)
Quando? 5 sessões: 4ªfs e 6ªfs (18h00 às 21h30) – 12, 14, 19, 26 de abril e 3 de maio de 2023.
Como se inscrever? Poderá efetivar a sua inscrição através do formulário de inscrições aqui. Terá de anexar os seguintes documentos: CV, Certificado de Habilitações, Comprovativo de Pagamento e Carta de Motivação.
Qual o valor e prazo da inscrição? Até 1 abr, a inscrição é de 180€. Após esta data, o valor será de 250€.
Quais são as condições para a atribuição de Bolsa UEPID? Será atribuída 1 Bolsa UEPID, no valor de 75% da inscrição. Poderá consultar o regulamento da Bolsa aqui
Para mais informações poderá visitar a página do curso aqui ou contactar-nos pelo email: mepidemiologia@medicina.ulisboa.pt
Pré-Inscrições Abertas: Novas Datas
II Curso Pós-Graduado de Sistemas de Informação Geográfica em Epidemiologia (presencial / à distância)
Onde? Presencial e à distância (em tempo real)
Quando? 8 sessões: 11, 15, 18, 22, 26, 29 de abril, 2 e 9 de maio de 2023. Para mais informações sobre o programa e tópicos das aulas, clique aqui.
Este curso inclui 1 licença do software ArcGIS Pro durante 1 ano
Como se inscrever? Através do formulário de pré-inscrições (link). Posteriormente receberá um email para efetivar a sua inscrição em que terá que enviar os seguintes documentos: CV, Carta de Motivação, Comprovativo de Pagamento e Certificado de Habilitações
Qual o valor e prazo da inscrição? Até 1 de abr, o valor da inscrição é de 275€. Após 1 de abr, a inscrição é de 350€.
Quais são as condições para a atribuição da Bolsa UEPID? Será atribuída 1 Bolsa UEPID, com o valor de 75% da propina. As candidaturas à Bolsa estão abertas até 1 de abr. Poderá consultar o regulamento da Bolsa aqui.
O curso conta com o apoio institucional da ESRI Portugal.
Para mais informações, clique aqui para visitar a página do curso ou contacte nos pelo email: mepidemiologia@medicina.ulisboa.pt
Novas Datas
I Curso / II Workshop de Gestão de Projetos Científicos em Saúde
Onde? à distância, em tempo real
Quando?
Curso (Componente Teórica + Laboratório de Competências): 3ªfs (18h00 -20h50) – 2, 9, 16, 23, 30 de maio e 6 de junho de 2023 e 6ªfs (18h00 – 20h50) – 5, 12, 19, 26 de maio e 2 de junho de 2023
Workshop (Componente Teórica): 3ªfs (18h00 -20h50) – 2, 9, 16, 23, 30 de maio e 6 de junho de 2023
Como se inscrever? Preencha o formulário de pré inscrições aqui
Qual o valor e prazo da inscrição?
Curso (Componente Teórica + Laboratório de Competências) – Até 22 de Abril de 2023, o valor será de 220€. Após esta data, a inscrição será de 320€.
Workshop (Componente Teórica) – Até 22 de Abril de 2023, o valor será de 170€. Após esta data, a inscrição é de 280€
Quais são as condições para a atribuição das Bolsas UEPID? Será atribuída até 1 Bolsa de Formação para o Curso e para o Workshop, no valor de 75% da inscrição. Para mais informações consulte o link
Para mais informações, clique aqui
Poderá também saber mais sobre o curso, através do vídeo aqui
Caso tenha alguma dúvida, por favor contacte nos pelo email: mepidemiologia@medicina.ulisboa.pt
Inscrições Abertas
XI Curso Pós-Graduado de Introdução aos Modelos Estatísticos em Epidemiologia
Onde? À distância (em tempo real)
Quando?
O curso irá decorrer aos sábados das 09h às 13h30 (hora de Lisboa) e terá 7 sessões: 18 mar, 1, 15, 29 abr, 13, 27 mai, 17 jun (avaliação). Aula de dúvidas opcional agendada para o dia 16 jun.
Haverá uma aula extra de introdução ao SPSS e revisão dos principais conceitos base no dia 15 de março (4ªf) das 18h às 21h.
Como se inscrever? Através do formulário de inscrições (link). Posteriormente receberá um email para efetivar a sua inscrição com os seguintes documentos: CV, Carta de Motivação, Comprovativo de Pagamento e Certificado de Habilitações
Qual o valor e prazo da inscrição? Até 9 de Mar, o valor da inscrição é de 280€. Após 9 de Mar, o valor será de 350€. As inscrições terminam no dia 14 de Mar.
Quais são as condições para atribuição da Bolsa UEPID? Este curso conta com uma Bolsa de Apoio UEPID que abrange 75% da propina. Para mais informações sobre a Bolsa, consulte o regulamento aqui
Para mais informações, clique aqui para visitar a página do curso ou contacte nos pelo email: mepidemiologia@medicina.ulisboa.pt
Pré-Inscrições: Cursos Pós Graduados
VI Curso Pós Graduado de Introdução à Investigação Epidemiológica
Onde? à distância (em tempo real)
Quando? 23 e 30 de março, 13, 17, 20, 27 de abril, 4, 11 de maio e 6 de julho (seminário) de 2023 – 5ªfs das 17h30 às 20h50 e 2ªfs das 14h30 às 18h00 (Hora de Lisboa)
Como se inscrever? Através do formulário de pré-inscrições (link). Posteriormente receberá um email para efetivar a sua inscrição com os seguintes documentos: CV, Carta de Motivação, Comprovativo de Pagamento e Certificado de Habilitações
Qual o valor e o prazo da inscrição? Até 15 de Mar’23, o valor da inscrição é de 310€. Após 15 de Mar’23, o valor será de 350€. As inscrições terminam no dia 22 de Mar.
Quais são as condições para a atribuição de Bolsa UEPID? Este curso conta com uma Bolsa de Apoio UEPID que abrange 75% da propina. Para mais informações sobre a Bolsa, contacte nos pelo email: mepidemiologia@medicina.ulisboa.pt
Para mais informações, clique aqui para visitar a página do curso
Cursos Pós Graduados: Inscrições Abertas
XV Curso Pós Graduado de Atualização – Construção, Validação, Aplicação e Interpretação de Questionários
Onde? à distância, em tempo real. Todas as aulas são videogravadas
Quando? 6 sessões: 16, 23 de fev; 2, 6, 9, 16 de mar (2ªfs, 14h30-18h00 e 5ªfs, 17h30-20h50 – hora de Lisboa)
Como se inscrever? Preencha o formulário de inscrição aqui
Qual o valor e prazo de inscrição? Até 9 fev’23, a inscrição é de 350€. Após 9 fev’23, o valor será de 420€.
Quais são as condições para a atribuição de Bolsas UEPID? Será atribuída 1 Bolsa UEPID, no valor de 75% da inscrição. Regulamento disponível aqui
Para mais informações, clique aqui.
Poderá também saber mais sobre o curso, através do vídeo (link)
Cursos Pós Graduados: Inscrições Abertas
Workshop Métodos Qualitativos (à distância)
Quando? 23, 26 de jan, 2, 6, 9 de fev 2023 (2ªfs, 14h30-18h00 e 5ªfs, 17h30-20h50 – hora de Lisboa)
Como realizar a inscrição? Inscreva-se aqui. Será necessário juntar: CV resumido, carta de motivação, certificado de licenciatura/mestrado (digitalizado) e comprovativo de pagamento.
Para consultar o regulamento da Bolsa UEPID, clique aqui.
Para mais informações consulte a nossa página.
Cursos Pós Graduados: Inscrições Abertas
Introdução à Bioestatística (à distância)
Quando? 5 e 19 de Novembro, 3, 17 de Dezembro de 2022, 7,21 de Janeiro, 4, 18 de Fevereiro, 3 e 4 de Março de 2023. Quinzenalmente aos sábados, das 09h às 13h30 ou das 11h-15h30 (horário de Lisboa).
Como realizar a inscrição? Inscreva-se aqui. Será necessário juntar: CV resumido, carta de motivação, certificado de licenciatura/mestrado (digitalizado) e comprovativo de pagamento.
Para consultar o regulamento da Bolsa UEPID, clique aqui.
Para mais informações consulte a nossa página.
terça-feira, 4 de outubro, 18h30-19h30
(sessão pelo zoom, hora de Lisboa)
O que se aprende, que competências, que modelo de formação?
Como são organizadas as sessões?
Posso repartir as unidades curriculares e realizar o Curso de Especialização em 2 anos?
Qual o valor e os critérios de atribuição das Bolsas de Apoio?
Que teses têm sido desenvolvidas? Cursos e conteúdos obrigatório e opcionais.
Quais as oportunidades atuais para se desenvolver investigação clínica e epidemiológica?
Registe o seu interesse na sessão: aqui.
Participação à distância, link a ser enviado por email.
- Instagram: https://www.instagram.com/uepid.fmul/
- Youtube: Unidade de Epidemiologia do Instituto de Medicina Preventiva e Saúde Pública
”Como ‘mapear uma área científica’? uma aula prática”
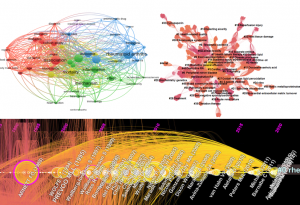
Docente: Paulo Jorge Nicola
Unidade de Epidemiologia, Instituto de Medicina Preventiva e Saúde Pública Faculdade de Medicina da Universidade de Lisboa
Resumo: Sempre que se faz uma pesquisa bibliográfica (por exemplo, no pubmed, no scopus ou na web of science), os resultados são uma lista de documentos. Se o propósito for ‘mapear a floresta’, fazer uma pesquisa bibliográfica equivale a ‘conhecer a floresta vageando pelos seus caminhos’. Pode-se contar com artigos de revisão, mas estes terão a perspectiva dos seus autores e um número limitado de referências. Realizar um ‘mapeamento de uma área científica’ é uma nova ferramenta e um conjunto de técnicas que permite ‘mapear a floresta’, analisando todos os documentos indexados e publicados nessa área. Estes podem ser vários milhares. Esta informação pode ser analisada quanto aos seus temas, tópicos, indicadores de impacto e de qualidade científica e sua evolução ao longo do tempo. Como os tópicos se relacionam entre si e interconectam disciplinas científicas distintas, trazem importantes ‘insights’ quanto à riqueza que dificilmente se revelarão com a análise de artigos individuais.
Assista ao vídeo da aula aberta aqui.
”Avaliação de Impacte na Saúde”

Profª. Doutora Leonor Bacelar Nicolau
Doutorada em Ciências e Tecnologias da Saúde/Organização e Gestão em Saúde pela Faculdade de Medicina da Universidade de Lisboa FMUL e Economia da Saúde pelo Conservatoire National des Arts et Métiers, França. Docente Convidada e Investigadora na FMUL (Instituto de Medicina Preventiva & Saúde Pública e ISAMB).
Assista ao vídeo da aula aberta aqui.
I Workshop Introdução à Gestão de Projetos de Investigação em Saúde
(à distância)

Quando? 10, 17, 24, 31 de maio e 7 de junho de 2022 das 18h00 às 20h50 (horário de Lisboa).
Onde? Curso à distância (em tempo real) ou presencial.
Como realizar a inscrição? Registe o seu interesse no formulário de pré-inscrição (link). Ser-lhe-à, posteriormente, enviadas instruções de inscrição.
Qual o valor e prazo para inscrição? Até 4 MAI’22, a inscrição é de 200€. Depois de 4 MAI’22 o valor será de 270€. Condições especiais para associações, sociedades e entidades académicas.
Para mais informações, clique aqui.
Análise Multifatorial em Epidemiologia (à distância ou presencial)
Quando? 25 e 27 de Maio, 1, 8, 22, 24 e 29 de Junho, 1,6 e 8 de Julho de 2022 das 18h às 20h50 (horário de Lisboa). Curso à distância (em tempo real) ou presencial.
Como realizar a inscrição? Inscreva-se aqui. Será necessário juntar: CV resumido, carta de motivação, certificado de licenciatura/mestrado (digitalizado) e comprovativo de pagamento.
Para mais informações, clique aqui.
Workshop Introdução à Plataforma Estatística “R” (curso à distância)

Quando? 20, 27 e 29 de abril, 3 e 10 de maio, das 19h00 às 22h30 (hora de Lisboa). Curso à distância, em tempo real.
Como realizar a inscrição? Inscreva-se aqui.
Para mais informações, clique aqui.
Introdução aos Modelos Estatísticos em Epidemiologia (à distância)

Quando? 23 e 26 de março, 9 de abril, 30 de abril, 14 de maio, 28 de maio, 4 de junho e 25 de junho de 2022, (aula de dúvidas a 24 de junho).
Como realizar a inscrição? Inscreva-se aqui. Será necessário juntar: CV resumido, carta de motivação, certificado de licenciatura/mestrado (digitalizado) e comprovativo de pagamento.
Para mais informações, clique aqui.
Construção, Validação, Aplicação e Interpretação de Questionários (curso à distância ou presencial)

Quando? O curso decorre nos dias 10, 17, 21, 24 e 31 de março, 4 de abril de 2022. Entrega do trabalho de grupo a 10 de abril.
Como realizar a inscrição?através do preenchimento do formulário de pré-inscrição aqui. O formulário de inscrição será enviado para todos os registados.
Para mais informações, clique aqui.

INTRODUÇÃO À EPIDEMIOLOGIA (curso à distância ou presencial)
Quando? 11 sessões: 5ªfs, 17h30- 20h50; 2ªfs, 14h30-17h50 – 4, 8, 11, 18, 22, 25 de novembro, 2, 6, 9, 16 e 20 de dezembro.
Como realizar a inscrição?através do preenchimento do formulário de pré-inscrição aqui. O formulário de inscrição será enviado para todos os registados.
Para mais informações, clique aqui.

ESPAÇO-PROJETO: Abordagem Prática à Investigação Epidemiológica(curso à distância ou presencial)